A Brief Introduction to the Right to Privacy – An International Legal Perspective
By Md. Toriqul Islam
Md. Toriqul Islam holds a Ph.D. from the Faculty of Law, University of Malaya, Malaysia, and is the research fellow at the Faculty of Law, University of Malaya, Malaysia.
Published January/February 2022
Table of Contents
1. Introduction
After the invention of computers in the 19th century and the Internet in the late 1960s, the vast majority of our work is done online. The dependence on online platforms has increased over the years, and people have begun using diverse online platforms for various purposes, including learning, business, entertainment, socialization, etc. The growing advancement in information and communication technology (ICT) has brought a radical transformation in the communicating process making life easier, faster, and smarter. This landscape also poses tremendous challenges to privacy, as numerous actors collect, store, and share our personal data with numerous third parties, mostly without our knowledge.
Over the last couple of decades, the collection, retention, use, and transfer of personal data have become rampant chiefly by government agencies and businesses. To indicate governments’ aptitude toward data processing, George Orwell once warned in his dystopian novel Nineteen Eighty-Four that Big Brother (government authorities) is always watching you.[1] This trend of government-sponsored data processing has increased significantly over time, especially after September 11, 2001.
While business’s data processing has also become evident by new business models that are mostly grounded on personal data. In course of time, the personal data market has become global due to the constant increase of the access and use of the Internet. Eventually, personal data has evolved as the main fuel of the 4th Industrial Revolution era. In such an atmosphere, ordinary citizens, being private individuals, or consumers desire to have adequate legal protections for their privacy rights. Thus, the worldwide debate on privacy concerns has become apparent. Keeping this in mind, this article aims to explore some basic aspects of privacy, including the meaning, value, historical development, challenges, and legal protections as ensured in international, regional, and national legal frameworks.
2. Meaning of Privacy
Privacy is an elusive and poorly defined conception.[2] Thus, much ink has been spilt in an attempt to define the term ‘privacy.’ In the era of information, privacy and technology shape and mold each other, and hence, privacy protection mechanisms would not work unless that is designed looking at the technological development. This context widens the trivial Cooley’s explanation of privacy ‘the right to be let alone’[3] to capture more complexities around privacy and allied economic, social, political, psychological and legal concerns. Generally, privacy refers to the condition or moral claim over others requiring abstaining from doing some specific activities.
Some scholars attempted to explain the notion of privacy demonstrating its synonym. Ruth Gavison, for instance, shares that privacy has some constituent components, such as anonymity, solitude and secrecy.[4] Whereas Helen Nissenbaum classified privacy as a dynamic and complex issue, and the sensitivity to the data in terms of the purpose, context, and trust.[5] Westin attempted to articulate privacy in terms of social, personal, and regulatory dimensions.[6] While Anita Allen concludes, privacy appears in the multifaceted denominations, e.g., physical, proprietary, decisional, informational, and so on.[7] Probably, one of the most referred definitions of privacy was given by D. W. Prosser in 1960.
Prosser explained, privacy is a group of the following four torts: (1) intrusion upon the plaintiff’s seclusion or solitude, or into his private affairs; (2) public disclosure of embarrassing private facts about the plaintiff; (3) publicity which places the plaintiff in a false light in the public eye; and (4) appropriation, for the defendant’s advantage, of the plaintiff’s name or likeness.[8] Being abstract, privacy encompasses numerous other issues, including the freedom of thought against surveillance; bodily integrity; protection of personal data; seclusion in residence; capacity of protecting reputation; safeguard against searches and questionings, etc.[9] In sum, privacy means one’s right to keep his/ her personal affairs and relationships away from the reach of others. A state of being alone, and thus, not to be interrupted or watched by others.
Indeed, the notion of privacy is full of disarray, and hence, there is hardly any definition of privacy that can satisfy everybody. At the same time, the evaluation and justification of privacy in society play a crucial role in rendering dimensions to the definition, and hence, an attempt of defining privacy would always be incomplete. Nonetheless, the following definition can satisfy many who searches for an inclusive definition of privacy.
Privacy is control over when and by whom the various parts of us can be sensed by others. By ‘sensed’ is meant simply seen, heard, touched, smelled, or tasted. By ‘parts of us’ is meant the part of our bodies, our voices, and the products of our bodies. ‘Parts of us’ also includes objects very closely associated with us. By ‘closely associated’ is meant primarily what is spatially associated. The objects which are ‘parts of us’ are objects we usually keep with us or locked up in a place accessible only to us.[10]
Privacy is a sweeping concept. Thus, over centuries, scholars from various disciplines aimed at defining privacy in diverse ways. Among all definitions, probably the simplest and most discussed legal definition of privacy is- ‘the right to be let alone’. Arguably, in the digital age, this typical definition of privacy cannot ensure the desired protection unless associated with control over information. Hence, many other authors used to define privacy in terms of information control.[11] The modern construction of privacy can be summarized by the following six headings: (1) the right to be let alone; (2) limited access; (3) secrecy; (4) control of personal information; (5) personhood, and (6) intimacy.[12]
From the above discussion, it has become explicit that the underlying meaning of the term ‘privacy’ is not generally unified, rather varies in diverse features, scopes, nature, culture, custom, moral value, etc. Although there are disagreements among scholars about the meaning of privacy, certain things are common in almost all discourses. All privacy-related discourses acknowledge- privacy is an intrinsic human right that facilitates individuals to exile outsiders from their intimate zones; uplifts the dignity of human beings, along with their other constitutional guarantees. Australian Privacy Charter, for instance, states that ‘privacy is such a value that underpins human dignity and other key values, such as the freedom of association, freedom of speech, etc. For details, see Australian Privacy Charter Council – The Australian Privacy Charter, AustLII, [1995] PrivLawPRpr 31, 1995 2(3) Privacy Law & Policy Reporter 44.
3. Value of Privacy
The evolving information age is transforming our lives in such a way that we could never imagine. In a data-based economy, privacy appears as one of the pressing concerns due to numerous reasons, such as globalization of human communication; commercial importance of data; interest of governments in accessing and processing of data; voluntary data sharing by people in social media; commercialisation of personal data; usage of cloud computing, and recognition of privacy as one of the fundamental human rights, e.g., freedom of speech.[13] In a networked world, diverse actors always monitor or track our activities, and consequently, our privacy witnesses tremendous threats. Indeed, privacy is indispensable, and hence, no one can violate privacy unless there remains a compelling State interest.[14]
Privacy is inevitable for not only human beings but also other animals. The basic outcomes of animal and cultural studies reveal that each of the animal species searches for privacy in a small group intimacy.[15] The ecological studies also show that the lack of intimate space, due to congestion and the like, causes tremendous threats to survival.[16] Adam Moore concluded that in the case of the absence of privacy, beasts could kill each other or be involve in suicidal reductions of their populations.[17] While conducting experiments on rats in cages, Calhoun witnessed that a certain portion of free space is crucial for each of the breeds. Any shortage thereof leads to splitting in amicable relations and causes illnesses, such as an increase of blood pressure, heart failure, etc.[18] Being a part of animal families, human beings also carry the same traits.
Privacy is crucial for democracy too, although the relationship between democracy and privacy is a complex and dynamic one. Even there remain disagreements also between them in terms of meaning, dimensions, types, etc. In recent years, the manipulation of voter’s psychology in social media by polling agents and eventually influences the result of the election have appeared as an issue of huge debate in the global political discourses. There are allegations against former US President Donald Trump that his election campaigns used the voter suppression strategy in the 2016 US election by sending negative messages, (dark posts) based on race, ethnicity and socio-economic status, using the advertising tools of Facebook.[19] The issue of voter suppression strategy is no longer restricted to the privacy of the individual voter, rather correlates to greater trends in democratic politics as well.
Above all, privacy matters because we all love to have an intimate life and like to share our stories and memories with only those whom we believe. Moreover, in pure democratic culture, personal liberty includes the autonomy and freedom of individuals from the unauthorized access of the business, and public and private actors. It would be disastrous, if any of these actors leak, in any way, our sensitive personal data. The losses will be unthinkable, as most of them are irreparable and admit no substitutes or compensations. Rotenberg remarked back in 1996 that ‘[p]rivacy will be to the information economy of the next century what consumer protection and environmental concerns have been to the industrial society of the 20th century’.[20] His anticipation has widely been explicit, as privacy emerges as one of the most desired interests in the contemporary world. Thus, from the cradle to grave, privacy requires to be duly respected.
4. Historical Development
Living life to the fullest, rights are inevitable. Thus, over time, numerous rights have been recognized as the natural outcomes of the economic, social, and political reforms. Although earlier, the law acknowledged a few rights only, such as the right to life, the right to property, etc., later, the law started acknowledging human feelings, emotions, intellects, etc. Gradually, the notion ‘right to life’ has been widened to cover ‘the right to enjoy life’, and ‘the right to be let alone’, which is alternatively known as ‘the right to privacy’.[21]
The notion of privacy has not matured overnight. It is argued that the discourse over privacy concerns is as old as human beings.[22] Aristotle was considered the first philosopher who distinguished the private spheres from the public spheres.[23] While the Romans advanced the notion of privacy and attempted to protect it judicially.[24] The notion can also be drawn back from several ancient codes as well, such as the Greek, Roman, and Anglo-Saxon codes.[25] Indeed, the notion of privacy has had long historical roots in both anthropological and sociological discourses. Aristotle’s demarcation on the public-private spheres of politics, i.e., the polis and oikos, is often identified as the formal reference to privacy.[26] It is believed that innovation and people’s inclination toward individualism are two responsible factors that cause a radical shift of privacy from the public to private and social domains, precisely known as the horizontal approach. Whereas the vertical construction restricts the notion in between the State-citizen’s relationship only.[27]
Although started with the view of protecting one’s bodily integrity and home from unwarranted intrusion, the notion of privacy turned soon toward control over personal information. Despite having a long history of evolution, the right to privacy has just been evident in the late 19th century. While the public attention encircling privacy has just escalated dramatically in the past centenary.[28] In particular, the modern construction of the notion was surfaced first in 1890 by Louis Brandeis and Samuel Warren’s scholarly piece ‘The Right to Privacy.[29] Henceforth, the notion of ‘privacy’ has become very popular; widely recognized and began to evolve as one of the fundamental human rights.
The main concerns as depicted in the work of Warren and Brandeis were the offensiveness and invasiveness in US journalism from the 1900s onwards. However, the essence of their article illustrated that technological advancement caused grave concern over privacy. Warren and Brandeis identified the press, instantaneous photography, newspaper, and numerous mechanical devices as the new threats to privacy.[30] Referring to the growing increase of the press and its threats to privacy, a study covering the periods 1850-1890 reveals that the circulation of the newspaper increased nearly 1000 per cent; from 100 papers with 800,000 readers to 900 papers with more than 8,000,000 readers.[31]
It may be argued that privacy, as we mean it today, is nearly a 150-year-old conception.[32] The history of privacy can be summarized as follows: (1) people began to build internal walls within a premise in nearly 1500 AD to ensure separate room for everyone; (2) praying and reading silently had been started as a popular habit from 1215 era; (3) people started using single bed from 1700 era; (4) people had been cautious about the privacy of information since the 1900s, especially, after the publication of Warren and Brandeis’ ‘The Right to Privacy’, and (5) privacy is about to finish again as it was in the early society after 1990s.[33]
In TechPrivacy, Professor Solove has interestingly chosen the use of cartoons to describe the history of privacy. Metaphorically, he demonstrates that the death of privacy has already started and will be continuing because of several scientific inventions, such as the portable cameras in the 1880s; telephone wiretapping in the 1890s; mainframe computers in the 1960s; personal computers in the 1980s; portable phones in the 1990s; portable computers in the 2000s; smartphones in the 2010s, and holographic life projection in the 2070s.[34]
It may be relevant to share that Westin classified contemporary privacy development into four phases, e.g., the first phase 1945–60; the second phase 1961–1979; the third phase 1980–1989, and the fourth phase 1990– 2002, respectively.[35] In line with Westin, the fifth phase (2003-ongoing) can be shown as the age of the Internet of things (IoT), ubiquitous computing, social media, Google and WikiLeaks, when the use of personal data has increased to an unprecedented level posing tremendous challenges to information privacy. Despite having references to privacy in diverse fields of study, and even in ancient texts, formal legal discourse over privacy had started and popularised just after Warren and Brandeis’s premier work, ‘The Right to Privacy’, as evidenced by numerous scholarly writings.[36]
5. Challenges of Privacy
Although the challenges of privacy have already been manifest, the current contexts require more detail on the issue. The nature, type, and extent of privacy invasions vary in ages, as ‘privacy law in general, and information privacy, in particular, have always been closely tied with technological development’.[37] The constant progress in diverse technologies, an increasing usage thereof, along with the large-scale processing of personal data, etc., immensely affect the conventional notion of privacy and the way of its invasion. Consequently, from the matters of secrecy, seclusion, bodily integrity, or inviolability of home, communication and correspondence, the worldwide focus of privacy issues has shifted nowadays to information privacy. Interestingly, throughout centuries, several Privacy Enhancing Technologies (PETs), such as encryption, metadata, application programming, system development governance, user interface, etc., are also being used for the protection of privacy.[38]
In the data-based economy, the production and promotion of technological devices and services largely rest on sharing data between individuals and businesses. Since most of our activities have become digitalized nowadays, numerous public-private actors can easily collect, retain, and analyse more data than in preceding periods. This milieu presents a chain interaction among technology, data, and privacy for this day and the days to come. It is not an exaggeration to say that ‘today’s world runs on personal data’.[39] Presumably, this landscape poses huge threats to privacy.
Having regard to the close connectivity between privacy intrusion and the use of technology of the ages, privacy challenges can be shown on different ages. The major privacy concerns in the past were mostly relating to trespass to house, correspondence, and communication, or intrusion against seclusion, mostly caused by the press, instantaneous photography, or the newspapers. Whereas the data breach incident appears as the major privacy concern this day, which is mostly caused by some technologies, such as wiretapping technology, lie detection technology, and the Internet. Hence, although trespassing and intrusion upon seclusion were the major privacy dilemmas in the recent past, this has been shifted to the data breach incident this day and in the future.
Some authors share, our age relied too much on some extractive technologies, such as spectrographs, video lenses, transmitters, and computers, and all these technologies extracted mostly the personal data.[40] Whereas other groups of authors identified six emerging technologies, e.g., drones, human enhancement technologies, RFID-enabled travel documents, second-generation biometrics, second-generation DNA sequencing, and whole-body scanners that entail enormous impacts on privacy.[41] Apart from those, a recent exciting development is face-to-data (F2D), i.e., advanced face recognition technology that accesses to and processes the personal data of the individuals automatically based on the facial images linked with the names.[42] Additionally, due to the growing adoption of some other technologies, such as cloud computing, big data analytics, and the Internet of things (IoT), privacy witnesses imminent danger.
Indeed, in the digital age, there are countless factors, technologies, and actors that are liable to cause privacy intrusion. Hence, preparing a list of those factors, actors, and technologies is quite an impossible task. Nonetheless, some authors identify several other technologies that may cause major privacy challenges for today and coming days. These privacy-intrusive technologies include, inter alia, ubiquitous computing; IoT; smart cities; satellite data; blockchain; cryptocurrency; machine learning; Artificial Intelligence (AI); automation; ambient technology; neurolinguistics technology; memetic technology, and grid technology.[43] These days and in the coming days, people may also suffer due to identity theft, data mining, smart cards, key logger, and wireless networking.[44]
Above all, the constant advancement in science and technology and increasing dependence thereof is, among others, the main cause of privacy invasions for today and future days. Posner remarked, the constant progress of science and technology in the last few decades has led us to the edge of the Orwellian nightmare. These privacy and technological conditions may be regarded as the ‘technocratic modernism’ that poses huge threats to privacy and freedom.[45]
The trend continues since most modern technologies run primarily on personal data. While technology operates mostly on personal data, there remains anxiety of usage of that data in an unlawful, unfair and untransparent manner. Additionally, the collected personal data may be used other than the original purposes, inaccurately, and stored for a long period than usual. Moreover, there exist always apprehensions regarding the integrity and confidentiality of the processed and stored data. In all these cases, our valuable personal data is prone to be compromised, lost, or damaged. Arguably, it is impossible to predict all possible privacy invasions that may be caused by modern and future scientific technologies, and hence, the policymakers cannot prepare legal rules for each of the scientific innovations. The policymakers should establish an adequate data protection regime, equipped with specific rules, policies, or mechanisms to strike the balance among the interests of the key stakeholders, e.g., public agencies, businesses, and data subjects.
6. Legal Recognition and Protection of Privacy
The secret data leakage of Julian Assange in 2010; Snowden’s revelation in 2013; Panama Papers leakage in 2016; Paradise Papers disclosure in 2017, and Facebook Cambridge Analytica’s scandal in 2018 have shocked the global community.[46] In 2019, another data leakage of above 540 million Facebook users was revealed, and until April 2019, nearly 1. 885 million customers’ financial data was leaked from First American Financial Corporation.[47] In March 2020, around 5.2 million guests’ information was leaked from hotel Marriott International.[48] In April 2021, the sensitive personal data of around 500 million users of LinkedIn was allegedly scraped.[49] All these incidents make people worried and aware of their privacy interests. Therefore, privacy appears as one of the pressing dilemmas in the contemporary globe that requires holistic solutions.
In response, the United Nations (UN), the European Union (EU), and other international and regional entities along with individual States have adopted numerous legal and policy measures. At the domestic level, a total of 145 countries have already passed data privacy laws, while others are attempting to amend their existing ones.[50] However, the legal recognition and protection of privacy can be discussed under the following sub-heads: privacy in the international legal instruments; privacy in the regional instruments, and privacy in the national legal regimes.
6.1. Privacy in the International Legal Instruments
To compare with the national and regional instruments, privacy was first recognized by Article 12 of the Universal Declaration of Human Rights, 1948 (UDHR). Other than the UDHR, numerous other international instruments also contain isolated privacy provisions. The international instruments that incorporate isolated privacy provisions can be classified into two sub-heads, such as (1) the UN instruments and (2) the OECD instruments.
Hence, the international instruments with privacy provisions include, among others- (a) Universal Declaration of Human Rights, 1948 (UDHR); (b) International Covenant on Civil and Political Rights, 1966 (ICCPR); (c) Convention on the Rights of the Child, 1989 (CRC); (d) International Convention on the Protection of the Rights of All Migrant Workers and Members of Their Families, 1990; (e) UN General Assembly Guidelines Concerning Computerized Personal Data Files, 1990; (f) Reports of the UN Special Rapporteur on the Right to Privacy (2016-2020); (g) UN Personal Data Protection and Privacy Principles, 2018; (h) OECD Guidelines on the Protection of Privacy, 1980, and (i) Revised OECD Privacy Framework, 2013.
The UDHR, 1948: The UDHR is the first UN instrument that recognizes privacy as one of the most important human rights, although subsequently, the right has been recognized by numerous other international, regional, and domestic legal and human rights instruments. It can be argued that through the UDHR, the ‘right to privacy’ became an international human right before it was constitutionally recognized as a fundamental right.[51] To recognize privacy as one of the human rights, Article 12 of the UDHR is worded as follows: “No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks.”[52]
The ICCPR, 1966: 18 years later since the adoption of the UDHR, privacy was recognized in Article 17 of the ICCPR using a similar language to Article 12 of the UDHR. The only difference between the two documents lies in the fact that Article 17 of the ICCPR adds the word ‘unlawful’ two times; before the term ‘interference’ and ‘attacks’ in the texts of Article 12 of the UDHR. Article 17 of the ICCPR, for example, affirms that “No one shall be subjected to arbitrary or unlawful interference with his privacy, family, home or correspondence, nor to unlawful attacks on his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks.”[53]
The CRC, 1989: The Convention on the Rights of the Child, 1989 (CRC) is another important UN document that attempts to ensure, among others, a child’s privacy interest. Being adopted by the UN General Assembly (UNGA) Resolution number 44/25 of 20 November 1989, the CRC pledges for the protection of the diverse rights of the children, including the right to privacy. The privacy provisions of this convention are also comparable with Article 12 of the UDHR and Article 17 of the ICCPR. For example, Article 16 of the CRC affirms that “ No child shall be subjected to arbitrary or unlawful interference with his or her privacy, family, home or correspondence, nor to unlawful attacks on his or her honour and reputation. The child has the right to the protection of the law against such interference or attacks.”[54]
The International Convention on the Protection of the Rights of All Migrant Workers and Members of Their Families, 1990: The next UN initiative was the adoption of the International Convention on the Protection of the Rights of All Migrant Workers and Members of Their Families, 1990, which aims to protect various rights of the migrant workers and their family members, including privacy. Regarding the protection of privacy, this instrument contains the same wordings as the UDHR, ICCPR, and the CRC. Article 14 of the Convention, for example, states that “No migrant worker or member of his or her family shall be subjected to arbitrary or unlawful interference with his or her privacy, family, home, correspondence or other communications, or unlawful attacks on his or her honour and reputation. Each migrant worker and member of his or her family shall have the right to the protection of the law against such interference or attacks.”[55]
The Guidelines for the Regulation of Computerized Personal Data Files, 1990: Apart from protecting the right to privacy, the UN was found keenly careful about the protection of one’s personal data as well. This has been evident by the ‘Guidelines for the Regulation of Computerized Personal Data Files’ which was adopted by the UNGA through its Resolution number 45/95 of 14 December 1990. It is worth mentioning that the principles enshrined in the said Guidelines were mostly based on the key data protection principles outlined in the OECD Privacy Guidelines, 1980, and Convention 108 of the Council of Europe, 1981.
However, the short titles of those principles are – (1) principle of lawfulness and fairness; (2) principle of accuracy; (3) principle of the purpose-specification; (4) principle of interested-person access; (5) principle of non-discrimination; (6) power to make exceptions; (7) principle of security; (8) supervision and sanctions; (9) transborder data flows, and (10) field of application. For details of these principles, see UN General Assembly, Guidelines for the Regulation of Computerized Personal Data Files, 14 December 1990.
The Special Rapporteur on the Right to Privacy: The UN efforts and promises for the protection of privacy have also been manifestly apparent through the Reports of the UN Special Rapporteur on the Right to Privacy. In July 2015, the UN Human Rights Council appointed Professor Joseph A. Cannataci as its first-ever Special Rapporteur to work on the project ‘The Right to Privacy in the Digital Age’. He had been given mandates to do plenty of works, including collecting relevant information, identifying probable obstacles, participating in global initiatives, raising awareness, and submitting annual reports to the Human Rights Council and the General Assembly of the United Nations.[56] Professor Joseph A. Cannataci enthusiastically commenced his roles on the issue and has taken numerous initiatives during his tenure in office.
Since 2016, the UN Special Rapporteur on the right to privacy has placed a total of 11 annual reports covering, inter alia, the state of privacy at the beginning of 2016; critical areas of work for the protection of privacy in the digital age, 2016; governmental surveillance activities from a national and international perspective, 2017; big data and open data interim report, 2017; security and surveillance, 2018; big data and open data, 2018; privacy, technology and other human rights from a gender perspective, 2019; the protection and use of health-related data, 2019; security and surveillance, health data, and business enterprises use of personal data, 2020; preliminary evaluation of the privacy dimensions of the coronavirus disease (COVID-19) pandemic, 2020, and artificial intelligence and privacy, and children’s privacy, 2021. The researcher has summarized some key observations of the reports of the UN Special Rapporteur on the Right to Privacy and shared them in the following box.
|
Privacy has appeared in the centre of global political, judicial, and personal attention more than in prior times. Though some governments and their parliaments show hostile attitudes to privacy, the courts, especially in the US and Europe, have taken straightforward efforts to favour privacy. There has been the commodification of privacy as it appears in a selling point by some major vendors. This trend forces market to produce privacy-friendly technologies. The governments worldwide should take part in dialogues to discuss the appropriate roles of the States and governance mechanisms for some crucial issues, including surveillance, cyberspace, privacy, freedom of expression, and other civil rights. Privacy interferences must be judged based on their merits under article 17 of the ICCPR and other provisions of international human rights law. Several interferences, such as excessive requests for user’s data and the retention of such data by third parties may have both short and long-term deterrent effects on freedom of expression. Moreover, States should make sure that surveillance is conducted by an independent, unbiased, and competent judicial body demonstrating that such an operation is essential and proportionate to the legitimate aims. In the digital age, the convergence between State Practices and roles of corporations appears moderately new for many States. There should have ways at both national and international levels to strike the balance between the interests of both businesses and the human rights of the individuals on all digital platforms. Data appears and shall remain the major economic resources, like money or labour. The aggregate dependency on personal information requires reconciliation with privacy and data protection legislation. Economic and political actors usually underpin the methods and practices encircling open data. Nonetheless, in the capitalist economies, contemporary business models have little incentives for the protection of personal data as there exists no consequential economic loss in turn. Consumer law and data protection law are substantially complementary to each other. Devoid of data protection law, the sole reliance on consumer law means to refute the correlation between fundamental human rights and the remedies of their violations. While considering bills for the betterment of open data, the laws of the Member States must be adjusted to international human rights obligations; blended with best practices, and ethical values; prepared on data protection principles and appropriate regulatory models; blessed with adequate resources, independent regulator, and necessary definitions, including specific data-sharing, usage, exposure and publicity principles. The Universal Declaration of Human Rights urges each person and part of society to uphold and regard human rights. Therefore, States, businesses, civil society, professional groups, religious organizations, and private individuals have significant roles to play. Having the confidence of the individuals in gathering ideas and sharing is fundamental to numerous values, as well as democracy. Thus, the loss of privacy resembles the loss of confidence in government, public institutions, and the withdrawal from participation. The loss of privacy eventually, adversely affects and impairs the representative democracies. Privacy for women, children, diverse sexual orientations, and gender identities is crucially important. Particularly, the gender-based privacy invasion is a systemic denial of human rights. It is discriminatory, and constantly perpetuating to socio-economic, political, and cultural settings. Hence, this intrusion of privacy requires legal and regulatory frameworks at national, regional, and international levels. Gender should be one of the key considerations while developing and implementing privacy protection frameworks. To ensure a minimum response to a detailed and harmonised privacy regime at the international level, all Member States may ratify the Modernized Convention 108 along with its Protocol CETS 223, and implement their provisions through domestic law without delay. The Member States outside the EU may also incorporate the protections enshrined in the GDPR. Countries with no adequate data protection regimes, or not the members of the EU, should adopt the provisions similar, or superior to the GDPR for the protection of personal data online.[57] |
The statements in the above box are some selective remarks taken from the observations, concluding remarks, or recommendations of five UN Reports of the Special Rapporteur on the Right to Privacy (2016-2020). All these as shown here neither describe the whole idea presented in those five documents nor the sum total thereof, these are only some selected remarks that are compiled by the researcher. For details, see UNHRHC, ‘Annual Reports’, United Nations Human Rights Office of the High Commissioner.
The Personal Data Protection and Privacy Principles, 2018: The United Nation’s firm conviction on privacy and personal data protection has been made explicit by another notable initiative thereof, such as the ‘Personal Data Protection and Privacy Principles’, 2018. On 11 October 2018, the UN High-Level Committee on Management (HLCM), at its 36th Meeting, adopted a set of ‘Personal Data Protection and Privacy Principles’, which set forth the essential basis for the processing of personal data by, or on behalf of any organization of the UN while performing their scheduled activities.[58]
The aims of those principles include, inter alia, (i) harmonization of standards for the protection of personal data among organizations of the UN; (ii) facilitating responsible data processing for implementing the mandates of the organizations of UN; and (iii) securing respect for human rights, fundamental freedoms, and especially, the right to privacy.[59] The said document further notes that the principles contained therein will apply to personal data of any kind and be processed in any way. The detailed contents of those principles can be seen at CEB: UN System Chief Executives Board for Coordination, Personal Data Protection and Privacy Principles, 2018.
The Guidelines on the Protection of Privacy and Transborder Flows of Personal Data, 1980 (OECD Privacy Guidelines): During the 1970s, it was speculated that the data security rendered in national regimes were likely to be bypassed in trans-border data processing activities. This ground reality made it compelling that certain principles, rules or guidelines were to be farmed and agreed upon at the international level. Eventually, two international organizations, such as the Organization for Economic Cooperation and Development (OECD) and the Council of Europe (CoE) had attempted to formulate the guiding principles for the protection of privacy and harmonized data protection standards. On 23 September 1980, the OECD Council formally ratified the Guidelines on the Protection of Privacy and Trans-Border Flows of Personal Data that proceeded with the following objectives:
- To achieve certain minimum standards among the Member Nations regarding the protection of privacy, individual freedoms, and personal data;
- To reduce differences to a minimum degree among Member Nations regarding relevant national laws and practices;
- To extend cooperation among the Member States concerning the protection of personal data, avoiding undue interference regarding trans-national data flows, etc. and
- To eliminate all possible obstacles that may induce Member Nations to restrict transborder data flows on the ground of correlated risks.[60]
The OECD Privacy Guidelines was the first Trans-Atlantic agreement devised to protect data privacy that blended the policies of national legal regimes to international legal standards concerning flows of data.[61] Although the Guidelines did not have any compelling authority over its Member Nations but generated consensus concerning appropriate principles for data privacy. Importantly, the principles enshrined in the OECD Guidelines laid down the founding stones of modern data protection norms and principles. Greenleaf, for example, remarked, together with Convention 108 of Council of Europe 1981, the OECD Privacy Principles, 1980 placed the first-generation international data protection standards. The Directive 95/46/EC represents the second-generation standards, whereas the GDPR appears as the third-generation international data protection standards.[62]
From its inception, the OECD Privacy Guidelines had notable impacts on data privacy laws all over the world. Although it was a voluntary instrument, some basic principles have become parts of the law later. One of the basic features of the OECD Guidelines was that it applied to personal data of both the public and private sectors. Part Two of the OECD Privacy Guidelines contains basic (privacy) principles of national application. It includes eight data privacy principles, which form the basis of the privacy principles of both Directive 95/46/EC, and the EU GDPR, 2018. The precise titles of those principles include (1) collection limitation principle; (2) data quality principle; (3) purpose specification principle; (4) use limitation principle; (5) security safeguards principle; (6) openness principle; (7) individual participation principle; and (8) accountability principle. For details, see OECD, Guidelines on the Protection of Privacy and Transborder Flows of Personal Data, 1980.
The Revised OECD Privacy Framework, 2013: Being the first global initiative for the core data protection regulations, the OECD Privacy Guidelines 1980 generated huge implications throughout decades. In the words of Justice M. Kirby, the chair of the OECD specialist team, ‘the continual acceptance of the OECD for a long period of 30 years have proved the utility of the Guidelines, and it was anticipated too’.[63] Notwithstanding the overwhelming attainment, an accord was growing to revise the Guidelines. The modernization was required, as there raised inevitable questions as to the effectiveness of the Guidelines due to the evolution of the Internet; world wide web; search engines; social networking sites; location tracking technology; biometrics and other technologies, etc.[64] Finally, after conducting a rigorous review process, the OECD adopted the Revised Guidelines on 9 September 2013.[65] The Revised Guidelines offers the following novel strategies:
- National privacy strategies: While adequate laws are imperative, the strategic importance of privacy in this day entails a multi-layered national strategy in association with the highest level of governance.
- Privacy management programmes: This mechanism works as the central operational tool by which the organizations enforce the privacy protection.
- Data security breach notification: This provision comprises notices both to the authority and the individuals affected by the security breach of personal data.[66]
Above all, the Revised OECD Guidelines, 2013 approaches the transborder data flow and details the key elements that make it appear as a more responsible organization capable of enhancing privacy enforcement. Being a move toward a continuous process, this revised version of the Guidelines leaves the ‘basic principles’ intact of its original version. To know some more details, see OECD, OECD Privacy Framework, 2013.
6.2. Privacy in the Regional Instruments
The regional legal and human rights instruments that contain privacy provisions may be classified into two sub-groups, such as the non-EU instruments, and the EU instruments. Usually, most of the non-EU instruments do not hold any binding effect on the Member States, but the EU initiatives are generally binding on their Member Nations. The EU instruments have had immense implications not only on the data protection regimes of the Member States but also on other jurisdictions outside the EU.
6.2.1. The Non-EU Instruments
The major non-EU legal and human rights instruments, which comprise privacy provisions, include, among others, (a) American Declaration of the Rights and Duties of Man, 1948; (b) American Convention on Human Rights, 1969; (c) APEC Privacy Framework, 2004; (d) Updated APEC Privacy Framework, 2015; (e) Madrid Resolution, 2009; (f) ASEAN Human Rights Declaration, 2012, and ASEAN Framework on Personal Data Protection, 2016.
American Declaration of the Rights and Duties of Man, 1948: With several specific objectives, especially, the regional unity and collaboration within the Member Nations, the Organization of American States (OAS) emerged in 1948 by signing the Charter of the OAS in Bogotá, Colombia that came into effect in December 1951.[67] On 2 May 1948, the OAS adopted the American Declaration of the Rights and Duties of Man, which contains some provisions relevant to the protection of privacy.
Affirming the right to protection of honour, personal reputation, private and family life, etc, Article V of the said document states, ‘[e]very person has the right to the protection of the law against abusive attacks upon his honour, his reputation, and his private and family life’. Whereas Article IX and X guarantees the right to inviolability of the home and transmission of correspondence. Article IX states, ‘[e]very person has the right to the inviolability of his home’, while Article X asserts, ‘[e]very person has the right to the inviolability and transmission of his correspondence’.[68] It may be relevant to share that this Declaration, otherwise referred to as the Bogota Declaration, was the world’s second international human rights instrument of a general nature that was adopted less than one year after the adoption of the UDHR.
American Convention on Human Rights, 1969: The American Convention on Human Rights, 1969, otherwise known as the Pact of San José, was another notable initiative of the Latin-American developments in human rights, which was adopted on 22 November 1969 at the Inter-American Specialized Conference on Human Rights, San José, Costa Rica.[69] The document came into effect nine months later, i.e., after the 11th ratification instrument was placed on 18 July 1978. It is a massive instrument comprising a total of 82 articles, which affirms a plethora of civil and political rights,[70] including the right to privacy. For the protection of privacy, Article 11 of the said document states that “Everyone has the right to have his honour respected, and his dignity recognized. No one may be the object of arbitrary or abusive interference with his private life, his family, his home, or his correspondence, or of unlawful attacks on his honour or reputation. Everyone has the right to the protection of the law against such interference or attacks.”[71]
In 1979, an agreement was signed to create the Inter-American Court of Human Rights and the Inter-American Commission on Human Rights (IACHR), although the decisions of such Court are not mandatory on the Member Economies.[72] It is worth noting that both the American Convention on Human Rights, 1969, and the European Convention on Human Rights and Fundamental Freedoms, 1950 affirm the protection of privacy in the same language as enshrined in the ICCPR.
APEC Privacy Framework, 2005: The Asia-Pacific Economic Cooperation (APEC) is an inter-governmental platform for 21 Member Economies in the Asia Pacific regions, which promotes, among others, free trade across the region. The organization works on three broad pillars, such as (a) trade and investment liberalization, (b) business facilitation, and (c) economic and technical cooperation.[73] To promote e-commerce in the Asia Pacific region by emphasizing the value of privacy of personal information, the APEC alliance attempted to develop a privacy framework in 2003, which was adopted in 2004 and finalized in 2005.[74]
The APEC Privacy Framework comprises four major parts. Part I contains the preamble; Part II includes the scope; Part III contains nine information privacy principles, and Part IV covers the implementation. Like the OECD Privacy Guidelines, the APEC Privacy Framework comprises several privacy principles, such as (1) preventing harm principle; (2) notice principle; (3) collection limitations principle; (4) uses of personal information principle; (5) choice principle; (6) integrity of personal information principle, and (7) security safeguards principle. For details of the privacy principles, see APEC, APEC Privacy Framework, 2005.
However, the principles of the APEC Privacy Framework are not binding on the Member Economies, rather work as a harmonized basis for all regional privacy policies.[75] In the issue of trans-border data transfer, the Member Economies consented to co-operate through the national regulatory authorities. Moreover, the Framework nurses, among others, the doctrine of self-regulation.[76] Above all, the APEC Privacy Framework was considered as one of the most vital global privacy instruments after the Directive 95/46/EC.
Updated APEC Privacy Framework, 2015: The older version of the APEC Privacy Framework, 2005 was modelled on the OECD Privacy Guidelines, 1980. To cope with time and the day, the OECD revised its Privacy Guidelines in 2013. This backdrop leads APEC to revise its Privacy Framework in 2015 in light of the Revised OECD Guidelines 2013.[77] In the updated version of APEC Privacy Framework, the notable inclusions are, among others- Cross Border Privacy Rules System (CBPR System); APEC Cross-border Privacy Enforcement Arrangement (CPEA); Privacy Enforcement Authority (PEA); Privacy Recognition for Processors System (PRP System); Accountability Agents; Interoperability, etc.
The Updated APEC Privacy Framework, 2015 emphasizes the ‘interoperability’ in the privacy frameworks among the Member Economies. The APEC Economies recognize that personal data flows should not be stopped within the region, and accordingly, the Member States should promote and encourage interoperability in diverse privacy instruments to give effect to the APEC Privacy Framework itself. Moreover, the leaders of the APEC Economies are in the belief that the global interoperability of the privacy framework may also help individuals in asserting their right to privacy in a global context and assist the authorities to strengthen cross-border privacy enforcement.[78]
To compare with the OECD Privacy Guidelines, the APEC Privacy Framework is manifestly weaker due to, inter alia, the lack of some principles, such as the ‘purpose specification principle’ and the ‘openness’ principle. Contrarily, the APEC Privacy Framework introduced some new principles, absent in the OECD Privacy Guidelines, such as ‘preventing harm’, ‘choice’, and ‘due diligence in transfers’ features of the ‘accountability principle’. Some notable criticisms of the APEC Privacy Framework are- (1) APEC Privacy Framework imposes the burden of proof on the consumers, (2) APEC privacy principles apply only to natural persons, (3) the instrument speaks nothing about the automatic data collection processing or tools, such as the usage of cookies. In fine, the APEC Privacy Framework cannot achieve the desired goals unless the provisions of the Framework are enforced by the Member Economies, although neither the Framework fixes any date of commencement, nor it inflicts any penalty for infringement.
Madrid Resolution, 2009: The Madrid Resolution is another privacy and data protection instrument that was adopted by the national data protection authorities of 50 countries on 5 November 2009 through an international conference held in Madrid. The instrument introduced new values emphasizing the global nature of the right to privacy, along with the underlying principles and guarantees by rendering better protection for the rights of the individuals, especially in cross-border data flows. The Resolution comprised two folded purposes in specific terms, such as (a) defining a group of principles and rights ensuring an active and globally harmonized protection for the privacy of personal information, and (b) facilitating the transborder flows of personal data, essential for the interconnected world.[79]
Like all other typical data protection instruments, the Resolution incorporated both the rights of the data subjects, e.g., the right of access, right to rectify, right to object, etc.,[80] and the duties of the controllers.[81] However, unlike other data privacy instruments, the Resolution required the data controllers to notify the data subjects about their data breach incidents.[82] The Document contained the following data protection principles (Basic Principles): (1) the principle of lawfulness and fairness; (2) purpose specification principle; (3) proportionality principle; (4) data quality principle; (5) openness principle, and (6) accountability principle.[83]
There are also novelties in the Resolution as put forward with the proactive measures, which was enumerated in Article 22 of the Resolution. These include (1) procedures to prevent and detect breaches; (2) appointment of data protection officers (DPOs); (3) periodic training, education and awareness programs; (4) periodic audits; (5) adaptation of information systems and/or technologies; (6) conducting privacy impact assessments; (7) adoption of codes of practice, and (8) implementation of a response plan.
Notably, after the adoption of the Madrid Resolution, numerous global giant corporations, such as Accenture, General Electric, Google, Hewlett Packard, IBM, Intel, Microsoft, Oracle, Procter & Gamble, and Walt Disney, endorsed a declaration welcoming this instrument.[84] The said declaration also affirmed that the Madrid Resolution incorporated such principles, procedures, rights, and obligations that any data protection regime should satisfy. Thus, the Resolution appeared as a pioneering step toward making an internationally binding data protection instrument and standard for data protection legislation.
ASEAN Human Rights Declaration, 2012, and ASEAN Framework on Personal Data Protection, 2016: The Association of Southeast Asian Nations (ASEAN) was formed on 8 August 1967 as a regional economic organization through signing the ASEAN Declaration by the five founding nations, such as Indonesia, Malaysia, the Philippines, Singapore and Thailand. Subsequently, five more Member Nations joined the forum to make up the present ten Member States of the ASEAN. In particular, Brunei Darussalam joined on 7 January 1984; Viet Nam on 28 July 1995; Lao PDR and Myanmar on 23 July 1997, and Cambodia on 30 April 1999.[85]
In 2012, ASEAN’s Intergovernmental Commission on Human Rights made the initial draft of the ASEAN Human Rights Declaration, which was adopted unanimously on 18 November 2012 at Phnom Penh, Cambodia. The Declaration affirms ASEAN’s commitment to human rights by comprising a total of 40 paragraphs under 6 headlines. Privacy, being one of the ‘Civil and Political Rights’, has been recognized in the Declaration in the same tone as in the UDHR, and ICCPR. Article 21 of the Declaration, for example, declares:
Every person has the right to be free from arbitrary interference with his or her privacy, family, home or correspondence including personal data, or to attacks upon that person’s honour and reputation. Every person has the right to the protection of the law against such interference or attacks.[86]
Whereas the ASEAN’s Framework on Personal Data Protection was adopted in a meeting of the Telecommunications and IT Ministers of ASEAN countries at Bandar Seri Begawan, Brunei Darussalam on 25 November 2016. Among others, the Framework includes seven Principles of Personal Data Protection, such as (1) consent, notification and purpose; (2) accuracy of personal data; (3) security safeguards; (4) access and correction; (5) transfers to another country or territory; (6) retention, and (7) accountability.[87]
The Framework aims to strengthen data protection in ASEAN and facilitates cooperation among the Member Nations. Besides, it serves to contribute, promote, and growth of regional and international trade, together with transborder flows of data. However, the Framework serves as a record only, and accordingly, it does not create any legally binding obligation either expressly or impliedly under domestic or international law.[88]
6.2.2. The EU Instruments
Europe is the home for the world’s oldest, comprehensive, and massive data privacy regulations ensuring at both national and regional levels. Through its transnational bodies, the EU establishes itself as a stepping-stone in the development of the global data protection framework. The EU data protection legal frameworks can be shown by four distinct periods, such as (1) national data protection regimes (1970-1980); (2) internationalization (1980-1981); (3) national implementation (1982-1994), and (4) European harmonization (1995-2016/ 2018).[89]
It is noteworthy that through its approach to adopting comprehensive privacy regulations, the EU challenges the US dominance in the field. The notable EU instruments with immense global implications include, inter alia, (a) European Convention on Human Rights and Fundamental Freedoms, 1950; (b) Convention of Council of Europe, 1981; (c) Modernized Convention of Council of Europe (Convention 108+), 2018; (d) Directive 95/46/EC, 1995, and (e) General Data Protection Regulation, 2018 (GDPR).
European Convention on Human Rights and Fundamental Freedoms, 1950: The European Convention on Human Rights and Fundamental Freedoms, 1950 is the first convention and landmark instrument of the entire data protection initiatives of the Council of Europe. The Convention was adopted in 1950 and came into effect in 1953, the ratification of which was a requirement to join the Council.[90] The Convention protects, among others, the right to respect for private and family life. Article 8 of the Convention, for example, affirms:
Everyone has the right to respect for his private and family life, his home and his correspondence. There shall be no interference by a public authority with the exercise of this right except such as is under the law and is necessary for a democratic society in the interests of national security, public safety or the economic well-being of the country, for the prevention of disorder or crime, for the protection of health or morals, or the protection of the rights and freedoms of others.[91]
The European Court of Human Rights (ECHR or ECtHR) is accountable for the implementation of the Convention among the 47 Member Nations of the Council of Europe. Individuals can also bring complaints against the violation of human rights to the ECHR after they have utilized all possible chances of appeal at the national level.[92] It may be relevant to share that from its establishment in 1959, the ECHR has delivered over 16,000 judgments resulting in significant changes to the EU laws and helped to strengthen the rule of law in the region.[93]
Convention 108 of the Council of Europe, 1981: The Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data, 1981,[94] popularly known as the Convention 108 of the Council of Europe is deemed as one of the crucial data protection instruments to be known as the ‘crowning achievement in the domain of data protection after OECD Guidelines’.[95] Convention 108 was adopted and opened for signature in 1981, and it became effective from 1985. Although the Convention was adopted within a regional arrangement, turned later into the first binding international treaty. This has been witnessed through the accession of Convention 108 by the non-EU Member States since 2013.
The central focus of the Convention 108 was not to interpret privacy or personal data, rather impose certain limitations on the processing of some sort of sensitive personal data. Such limitations are needed because of the increasing use of computers in organizational activities resulting in tremendous challenges to data privacy. Convention 108 binds all signatories to have certain legislative steps domestically, and this is why Convention 108 had an influential impact on the major European legal frameworks. Convention 108 goes on isolation with nations having no privacy laws or data harbors. Eventually, most of the nations in the European zone have been bound to enact the data privacy bills.[96] Among others, Chapter II of the Convention (Articles 4-11) incorporates the basic principles for data protection. The essence of these principles renders wider scopes to suit them in diverse legal and constitutional practices in the region.
In 2001, the Council of Europe felt necessary to amend some provisions of Convention 108. Accordingly, it introduced some essential changes regarding the national supervisory authorities and transborder data flows to non-Member States. The amendment commenced with the consultative committee thereof, which produced a report requiring the evaluation of the Convention against the challenges of the emerging ICTs. The report also identified some issues, challenges, or dilemmas encircling the implementation of Convention 108 to which modernization is the only possible approach to adopt. In turn, an Additional Protocol regarding the supervisory authorities and transborder data flows was approved in August 2001.[97]
The Convention 108 allows the collection and processing of personal data, but without taking adequate legal safeguards, it restricts the processing of some sorts of sensitive data, such as one’s race, sex, or health data, data relating to one’s sexual life, religious, or political views, criminal records, etc. The Convention also affords individuals the right to know about the stored personal data about them and to have it corrected if necessary. Restrictions on the exercise of this right of the individuals are guaranteed only on questions of compelling State security, national defense, public interests, etc. Moreover, the Convention imposes restrictions on transborder data transfer if the third countries do not ensure adequate legal safeguards for the protection of personal data.[98]
From November 2004, the European Council was found enthusiastic about sharing personal data for safety and security reasons. The Hague Program allowed the law enforcement agencies within the EU to enter into extensive databases of personal data and biometric data. In November 2012, the T-PD Committee adopted an updated version of Convention 108 and its additional protocol to modernize Convention 108 entirely. The updated version of the Convention 108 is now advancing in multiple avenues. With all Council of Europe’s data protection efforts, with the OECD Privacy Guidelines, 1980, and the Convention 108, together they have set the global standards for data privacy regulations.[99]
Modernized Convention of Council of Europe (Convention 108+), 2018: Even though the core privacy principles of the Convention 108 had passed the test of time, and its technologically neutral and principle-based approach created an unquestionable strength, the Council of Europe felt essential to modernize its benchmark instrument. For the modernization process, the Council of Europe adopted the amending Protocol (ETS No. 108) in its 128th Session of the Committee of Ministers, held on 17-18 May 2018 at Elsinore, Denmark, followed by a public consultation that started from 2011.[100] After seven years of intense deliberation and dialogue, Convention 108, the only globally binding data protection instrument finally had been modernized in May 2018.
There were two main objectives behind this modernization, such as addressing privacy challenges arising out of the use of the new information and communication technologies and enhancing the implementation mechanisms of the Convention.[101] However, the novelties of Modernized Convention 108 can be summarized as follows:
- The modernized Convention introduced some new rights for the data subjects, e.g., the rights not to be subject to automated decision making, profiling, and algorithms; the right to object, etc.
- Although the modernized Convention keeps the original data protection principles intact, strengthens some of them, and importantly, adds several new protections.
- Biometric data and genetic data have been added to special categories of data.
- It imposed certain new obligations on controllers, such as accountability, transparency, data breach notification, risk assessment, privacy by design and by default, etc.
- It updated the provisions regarding the trans-border data flows, and wherever appropriate, extended these obligations to data processors.
- It strengthened the powers of supervisory authorities and emphasised cooperation for the accomplishment of their duties.
- The modernized Convention established a monitoring mechanism to ensure that the signatories respect their obligations under the Convention.[102]
Besides, the modernized Convention 108 added additional requirements for numerous issues, including the sensitive data; anonymization of personal data; appointment of the independent Data Protection Authority (DPA); remedies of courts, restrictions on data transfer, etc. Thus, it has become evident that the standards offered by the modernized Convention 108 are manifestly higher than the standards of the previous Convention 108 and its Additional Protocol of 2001.
Moreover, based on the provisions of Article 23 (Accession by non-Member States ) of the Convention 108; Article 27 (Accession by non-Member States or international organizations) of the modernized Convention 108; Recital 105 (Consideration of International Agreements for an Adequacy Decision) of the GDPR, and coupled with the wishes of the leaders of the Council of Europe, the modernized Convention 108 is gradually making it manifest that it is the only viable data privacy agreement across the globe. Although the globalization of Convention 108+ is a too ambitious goal, as evidenced by the slow rate of adoption of the document since 2013, it is nevertheless, becoming globalized through its accession outside Europe.
Directive 95/46/EC, 1995: The Council of Europe has had many success stories in devising numerous initiatives for ensuring the protection of privacy, processing of personal data, and the free flows of data. At the same time, the Council witnessed several challenges too in terms of maintaining consistency in all its data protection measures among the Member States. Therefore, it was essential to take an attempt for the harmonization of the regional data protection means and measures at the national level. After almost five years of intense initiatives and negotiations, this was succeeded by the adoption of ‘Directive 95/46/EC on the Protection of Individuals with regard to the Processing of Personal Data and On the Free Movement of such Data’ (Directive 95/46/EC) on 24 October 1995.[103] The provisions of this instrument have lost their previous status and importance due to subsequent abolishment by the GDPR, 2018.
General Data Protection Regulation (GDPR), 2018: Appearing as a buzzword, the GDPR has had immense implications on global data protection regulations. Based on omnibus legal substance, extensive extraterritorial scope, and influential market power of the EU, the GDPR diffuses globally as a standard for data protection law.[104] Therefore, it has become a trend of enacting or amending the existing data privacy legislation in conformity with GDPR across the globe. The roles, influences, legal, textual, and contextual highness of GDPR reach such a landmark and diffuses globally in a manner that one must have a minimum understanding about the acronym ‘GDPR’ unless living under the rock.[105]
The lifecycle of GDPR began in January 2012 through a proposal of the European Commission (EC), which was approved on 27 April 2016, and finally, came into effect on 25 May 2018. It replaced the previous Directive 95/46/EC with several intense changes in almost everything, ranging from technology to advertising, and medicine to banking.[106] It is considered as one of the most comprehensive and far-reaching pieces of Regulations, which address all possible challenges that people might face regarding their personal data in the digital age. After the adoption of the GDPR, it is argued that now the EU residents would know how businesses use their data, and how can the EU utilize the best opportunities of the data-based economy. Generally, companies required clarity to extend business operations safely throughout the region, and recent data scandals required to have clearer and stricter data protection regulations, and given this, the EU performed the right job.[107]
Under Article 3, the GDPR applies against any data controller or processor with an establishment in the EU, which processes personal data of the EU residents regardless of the place of such processing. Even the GDPR applies against foreign controllers or processors, who process the personal data of the EU residents by offering goods or services and monitor their behavior. Therefore, the long arm of GDPR is extended to cover the whole world, holding the view that you are targeted by EU law if you target or monitor EU residents.[108] This extraterritorial application of the GDPR gives rise to tension worldwide as non-compliance thereof leads to severe fines and penalties of up to €20 million or 4% of annual turnover, whichever is higher.
Thus, the implications of GDPR are not the hypothetic possibility, rather a true reality and these have been evidenced by the wave of GDPR-creep data protection legislation across the globe. Besides, global tech giants are shaping their business models in compliance with the provisions of the GDPR. Microsoft, for example, proclaimed to treat all users under the rules of the GDPR regardless of their location and empower them to customize their personal data accessing to the personal dashboard. Facebook has changed their privacy settings and tools in compliance with the GDPR.[109] Meanwhile, Google has updated its products and privacy policies in conformity with the GDPR.[110] Even Google made its privacy policy simple and clearer than earlier to conform to European law.[111]
Notably, the GDPR is a huge, comprehensive, and complex document containing 11 chapters; 196 recitals; 99 articles, and 88 pages with 55,000 words. Chapter I includes the ‘General Provisions’ covering, inter alia, (1) subject-matter and objectives (art 1); (2) material scope (art 2); (3) territorial scope (art 3), and (4) definitions (art 4). Chapter II includes the key privacy principles, such as (1) principles relating to the processing of personal data (art 5); (2) lawfulness of processing (art 6); (3) conditions for consent (art 7); (4) conditions applicable to child’s consent (art 8); (5) processing of special categories of personal data (art 9) and (6) processing of personal data relating to criminal convictions and offences (art 10).
Chapter III includes a wide range right of the data subjects, including- (1) right to transparent information (arts 12-14); (2) right of access by the data subject (art 15); (3) right to rectification (art 16); (4) right to erasure (right to be forgotten) (art 17); (5) right to restriction of processing (art 18); (6) right to data portability (art 20); (7) right to object (art 21), and (8) right not to be subject to automated decision making and profiling etc (art 22). The other chapters include numerous important provisions, such as Chapter IV: the obligations of the controllers and processors (arts 24-43); Chapter V: the transfers of personal data to third countries or international organizations (arts 44-48); Chapter VI: independent supervisory authorities (arts 51-54); Chapter VII: cooperation and consistency (arts 60-63); Chapter VIII: remedies, liability and penalties (arts 77-84); Chapter IX: provisions relating to specific processing situations (arts 85-91); Chapter X: delegated acts and implementing acts (arts 92-93), and Chapter XI: final provisions (arts 94-99).
Among others, the GDPR has tremendous effects on how data is managed within the EU and plays a significant role in shaping global data protection regulations. Recently, the UN Special Rapporteur on the right to privacy, for example, remarks that ‘[t]he protection of personal information online should be a priority with the adoption of provisions equivalent or superior to GDPR, for countries that are not parties to the Regulation’.[112]
Consequently, many countries in Europe other than the EU Member States, such as Iceland, Liechtenstein, Norway and Switzerland changed their data protection laws in harmony with the GDPR.[113] Even other than Europe, numerous other countries from Africa, Asia, the Caribbean and Latin America are either enacting new data privacy laws or amending previous laws in line with the GDPR.[114] Law firm Ius Laboris show that there are at least 24 countries outside the EU in which there exist GDPR-related legal developments, decisions, or trends of harmonization.[115]
Even the inclination of enacting a comprehensive data privacy bill at the US State level is very high than in previous times. Following the footstep of the CCPA, the Maine and Nevada States have also enacted the comprehensive bill. Many other US States, including Hawaii, Illinois, Massachusetts, Minnesota, New Jersey, New York, Pennsylvania, Rhode Island, and Washington have either introduced the comprehensive data privacy bills or have draft bills undergoing the examination process.[116] Indeed, GDPR-styled privacy standard is found not only in the ‘First World’, but also in the ‘Second World’, and the ‘Third World’ countries.[117] Hence, Giovanni Buttarelli refers to the GDPR as a clarion call for a unique global data privacy gold standard.[118] Whereas Paul M. Schwartz remarks that “EU data protection law is playing an increasingly prominent role in today’s global technological environment. The cornerstone of EU law in this area, the General Data Protection Regulation (GDPR), is now widely regarded as a privacy law not just for the EU, but for the world.”[119]
6.3. Privacy in the National Legal Regime
The trend of collecting personal data is as old as human society. It might not be the oldest profession, but one of the oldest habits.[120] In particular, since the 1960s onwards, the use of personal data has been dramatically increased because of the paradigm shifts in socio-economic and industrial settings.[121] In administering this bulk of reforms activities, the governments were to process huge amounts of personal data, and this data processing has become rampant after the emergence of the computer.
Initially, the computer was employed in research and planning works, but subsequently, it started operating in every sphere of human affairs. The creation of the Internet, the World Wide Web (WWW), and the constant progress of ICT technologies facilitated the collection, processing, and storing of large-scale personal data.[122] Later, big data analytics, cloud computing, data mining, artificial intelligence, machine learning, IoT technologies, etc. have revolutionized some emerging business models that process personal data to an unprecedented level. This atmosphere requires comprehensive data protection regulations to strike the balance among the interests of the government, businesses, and data subjects.
To respond, there has been a global trend of adopting data privacy legislation since the 1970s. Starting from the Hessian Data Protection Act, 1970 (Hessisches Datenschutzgesetz) of Germany, many other Western nations, including Austria, Denmark, France, Norway, Sweden, and the USA adopted privacy legislation in the early 1970s. Arguably, the Hessian Data Protection Act was considered a regional endeavour, whereas Sweden was the first nation to enact the data protection law (Datalagen 1973) in the world.[123] In the USA, the first federal legislative effort regarding privacy was the Privacy Act of 1974, even though the Fair Credit Reporting Act of 1970 contains several provisions of data privacy, e.g., provisions regarding credit reporting businesses, etc.
Following in the footsteps of Western countries, there has been a remarkable development in privacy enactments throughout decades. For instance, in the decade of 2010-2019, a total of 62 new countries enacted data privacy laws, which was significantly higher than the previous decade. In course of time, the per decade increase of the countries enacting data privacy laws appears very much impressive. The per decade number of countries enacting new data protection laws was 10 in the 1970s, 10 in the 1980s, 20 in the 1990s, 40 in the 2000s, and 62 in the 2010s.[124]
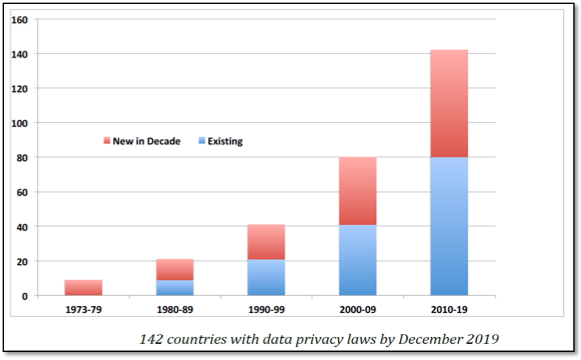
Figure 3.1: Per Decade Growth Rate of Data Protection Laws across the Globe.[125]
It is worthy of note that there are variances in approaches and models in data protection frameworks. Colin Bennett characterises four principal models of privacy management, such as- (a) licensing model (Sweden and Denmark adopted this model); (b) data protection commissioner model (adopting nations are Canada, New Zealand, etc); (c) registration model (the UK has taken this model), and (d) self-help and voluntary compliance model (the US adopted this model).[126] Banisar and Davis classified national privacy frameworks into three central models, such as the comprehensive model; the sectoral model, and the self-regulatory model.[127] Among these models of data protection frameworks, the US-based sectoral model and the EU based comprehensive model are most dominant. Although earlier, the US-based model of data protection was prevalent, now, the EU-based comprehensive model is prevailing as a data privacy standard in the world.
7. Conclusion
Privacy is one of the most valued human rights in the era of information. It is one of the pressing problems as well, because of the current digital contexts. Westin remarks, due to the increasing advancements in surveillance and psychological and physical technology, and their usage by diverse actors in the post-II World War era, privacy has become an ever-growing phenomenon.[128]
In the ubiquitous computing era, most of our activities are performed online using personal data. Consequently, personal data emerges as the new fuel to the Internet, and coin to the digital world. Nowadays, we are virtually present everywhere, from educational institutions to job places, and industrial sites to farmhouses. Arguably, this digital landscape makes life easier, faster and smarter but poses tremendous challenges to privacy. Hence, privacy appears as one of the hot-button issues in contemporary global politics, policies, and businesses. This context calls for holistic solutions and has led researchers to revisit privacy-related issues. Accordingly, this article outlines an overview of privacy, especially, the meaning of privacy, the value of privacy, historical development, associated challenges, legal recognition and protection of privacy, etc.
In response to diverse privacy challenges, the United Nations, the European Union, and other international and regional organizations, together with the individual States have adopted multiple legal and human rights instruments. There are several widely used policy measures, such as fostering privacy education; inspiring stakeholders in engagement; conducting awareness campaigning; ensuring transparency in surveillance practices; conducting privacy impact assessment and enacting the data protection legislation. Among these policy options, States are generally emphasizing the enactment since the 1970s. Among others, this article outlines the gradual development of privacy law and scholarship keeping international, regional, and national data protection frameworks in context. The findings of this article will enlighten all stakeholders regarding the emergence of the right to privacy from a global perspective together with a brief focus on all other associated issues.
[1] George Orwell, Nineteen Eighty-Four (Oxford University Press, 2021), part I, section I.
[2] Posner RA, ‘The Right of Privacy’ (1977) 12 Georgia Law Review 393.
[3] Thomas M. Cooley, A Treatise on the Law of Torts or the Wrongs Which Arise Independent of Contract (Chicago, Callaghan & Co., 2d ed. 1888) 29.
[4] Gavison R, ‘Privacy and the Limits of Law’ (1980) 89 The Yale Law Journal 421.
[5] Nissenbaum H, Privacy in Context: Technology, Policy, and The Integrity of Social Life (Stanford University Press 2009).
[6] Westin AF, ‘Social and Political Dimensions of Privacy’ (2003) 59 Journal of Social Issues 2.
[7] Allen AL, ‘Privacy-as-Data Control: Conceptual, Practical, and Moral Limits of the Paradigm’ (1999) 32 Connecticut Law Review 861.
[8] Prosser WL, ‘Privacy’ (1960) 48 California Law Review 383.
[9] Solove DJ, Understanding Privacy (Harvard University Press 2008).
[10] Parker RB, ‘A Definition of Privacy’ 27 Rutgers Law Review (1974) 275 281.
[11] Westin AF, Privacy and Freedom, Vol 7 (Atheneum 1967); Moore AD, Intellectual Property and Information Control (New Brunswick, NJ: Transaction Publishing 2001, 2004); Anita Allen, Why Privacy Isn’t Everything: Feminist Reflections on Personal Accountability (Lanham, MD: Rowman & Littlefield 2003), and Ruth Gavison, ‘Information Control: Availability and Control’ in Stanley Benn S and G. Gaus G (eds) Public and Private in Social Life (New York: St. Martin’s Press 1983) 113–34.
[12] Solove DJ, ‘Conceptualizing Privacy’ (2002) 90 California Law Review 1094.
[13] Kuner C and others, ‘The Extraterritoriality of Data Privacy Laws—An Explosive Issue Yet to Detonate’ (2013) 3 International Data Privacy Law 147-148.
[14] Elison LM and Nettik Simmons D, ‘Right of Privacy’ (1987) 48 Montana Law Review 1.
[15] Westin, Privacy and Freedom (n 11).
[16] Ibid.
[17] Moore AD, ‘Privacy: Its meaning and value’ (2003) 40 American Philosophical Quarterly 215, 221.
[18] Calhoun JB, ‘The Study of Wild Animals Under Controlled Conditions’ (1950) 51 Annals of the New York Academy of Sciences 1113.
[19] Bennett C and Oduro Marfo S, ‘Privacy, Voter Surveillance and Democratic Engagement: Challenges for Data Protection Authorities’ (International Conference of Data Protection and Privacy Commissioners (ICDPPC), October 2019) 7.
[20] James Gleick, ‘Big Brother Is Us’ The New York Times (29 September 1996), http://www.nytimes.com/1996/09/29/magazine/big-brother-is-us.html?pagewanted=all&src=pm.
[21] Warren SD and Brandeis LD, ‘The Right to Privacy’ (1890) Harvard Law Review 193-220.
[22] Holvast J, ‘History of Privacy’ (4th IFIP WG 9.2, 9.6/11.6, 11.7/, FIDIS International Summer School, Brno, Czech Republic, September 2008) 13.
[23] Smith R and Shao J, ‘Privacy and E-Commerce: A Consumer-Centric Perspective’ (2007) 2 Electronic Commerce Research 89.
[24] DeCew J, ‘Privacy’, The Stanford Encyclopedia of Philosophy (Spring edn, 2018) https://plato.stanford.edu/archives/spr2018/entries/privacy/.
[25] Hofstadter SH, Warren SD and Brandeis LD, The Development of The Right of Privacy in New York (Grosby Press 1954); Pound R, ‘Interests of Personality [Concluded’ (1915) 28 Harvard Law Review 445.
[26] DeCew ‘Privacy’ (n 25).
[27] Cofone IN, ‘Privacy Tradeoffs in Information Technology Law’ (DPhil thesis, University of Bologna 2015).
[28] Richie GE, ‘The Role of the Epistemic Community in Influencing Privacy Legislation: The United States and the European Union’ (DPhil thesis, University of Denver 2010).
[29] Warren and Brandeis (n 21) 195-196.
[30] Ibid.
[31] Solove DJ, Rotenberg M and Schwartz PM, Privacy, Information, and Technology (Aspen Publishers Online 2006) 9.
[32] Ferenstein G, ‘The Birth and Death of Privacy: 3,000 Years of History Told through 46 Images’, The Ferenstein Wire (25 November 2015), https://medium.com/the-ferenstein-wire/the-birth-and-death-of-privacy-3-000-years-of-history-in-50-images-614c26059e.
[33] Ibid.
[34] Solove DJ, ‘Cartoon: The History of Privacy’, TechPrivacy (26 January 2020), https://teachprivacy.com/cartoon-the-history-of-privacy/.
[35] See Westin ‘Social and Political Dimensions of Privacy’ (n 6) 6.
[36] Glancy DJ, ‘Invention of the Right to Privacy’ (1979) 21 Arizona Law Review 1; Shank R, ‘Privacy: History, Legal, Social, and Ethical Aspects and Privacy: Its Role in Federal Government Information Policy’ (1986) 35 Library Trends 7; Warren I, ‘The Right to Privacy in Nineteenth Century America’ (1890) 383 California Law Review 2960.
[37] Tene O, ‘Privacy: The New Generations’ (2011) 1 International Data Privacy Law 15.
[38] Steve Kenny, ‘An Introduction to Privacy Enhancing Technologies’, IAPP (1 May 2008), https://iapp.org/news/a/2008-05-introduction-to-privacy-enhancing-technologies/.
[39] Olano J, ‘The Struggle to Define Privacy Rights and Liabilities in a Digital World and the Unfortunate Role of Constitutional Standing’ (2018) 72 University of Miami Law Review 1025.
[40] Marx GT, ‘Privacy and Technology’ in Ola Espvik and others (eds) Telektronikk (Telenor 1996) 40.
[41] Finn RL, Wright D and Friedewald M, ‘Seven Types of Privacy’, European Data Protection: Coming of Age (Springer 2013), 6.
[42] Kuner C and others, ‘Face-to-Data–Another Developing Privacy Threat?’ (2013) 3 International Data Privacy Law 1.
[43] See, Holvast (n 22) 13.
[44] Ibid, 23-26.
[45] Posner RA, ‘Orwell Versus Huxley: Economics, Technology, Privacy, and Satire’ (2000) 24 Philosophy and Literature 1.
[46] Islam MT, ‘Abu Bakar Munir, Siti Hajar Mohd Yasin and Ershadul Karim, Data Protection Law in Asia’ (2018) 8 International Data Privacy Law 338.
[47] Holmes A, ‘Hackers have Become so Sophisticated that nearly 4 Billion Records have been Stolen from People in the Last Decade Alone. Here are the 10 Biggest Data Breaches of the 2010s’ Business Insider (New York, 13 October 2019), https://www.businessinsider.com/biggest-hacks-2010s-facebook-equifax-adobe-marriott-2019-10.
[48] Bethesda MD, ‘Marriott International Notifies Guests of Property System Incident’, Marriott News (31 March 2020), https://news.marriott.com/news/2020/03/31/marriott-international-notifies-guests-of-property-system-incident.
[49] Brown S, ‘14 of the Worst Data Leaks, Breaches, Scrapes and Security Snafus in the Last Decade’, CNET (23 April 2021), https://www.cnet.com/how-to/14-of-the-worst-data-leaks-breaches-scrapes-and-security-snafus-in-the-last-decade/.
[50] See generally, Greenleaf G, ‘Global Data Privacy Laws 2021: Despite COVID Delays, 145 Laws Show GDPR Dominance’ (2021) 169 Privacy Laws & Business International Report, 1, 3-5.
[51] Diggelmann O and Cleis MN, ‘How the Right to Privacy Became a Human Right’ (2014) 14 Human Rights Law Review 441.
[52] Universal Declaration of Human Rights (adopted 10 December 1948 UNGA Res 217 A(III) (UDHR) art 12.
[53] International Covenant on Civil and Political Rights (adopted 16 December 1966, entered into force 23 March 1976) 999 UNTS 171 (ICCPR) art 17.
[54] UN General Assembly, Convention on the Rights of the Child (adopted 20 November 1989) United Nations, Treaty Series, vol. 1577, art 16.
[55] UN General Assembly, International Convention on the Protection of the Rights of All Migrant Workers and Members of their Families (adopted 18 December 1990) A/RES/45/158, art 14.
[56] UNHRC, ‘Special Rapporteur on the Right to Privacy’, United Nations Human Rights Office of the High Commissioner, July 2015, https://www.ohchr.org/en/issues/privacy/sr/pages/srprivacyindex.aspx.
[57] These are some selective remarks taken from the observations, concluding remarks and recommendations of five UN Reports of the Special Rapporteur on the Right to Privacy (2016-2020). All these shown here neither describe the whole idea presented in those five documents nor the sum total thereof, these are selected statements compiled by the researcher. See generally, the details in UNHRHC, ‘Annual Reports’, United Nations Human Rights Office of the High Commissioner, https://www.ohchr.org/EN/Issues/Privacy/SR/Pages/AnnualReports.aspx, accessed 6 December 2020.
[58] UN High-Level Committee on Management (HLCM), Personal Data Protection and Privacy Principles (2018), https://www.unsceb.org/CEBPublicFiles/UN-Principles-on-Personal-Data-Protection-Privacy-2018.pdf.
[59] Ibid.
[60] OECD, ‘Guidelines on the Protection of Privacy and Transborder Flows of Personal Data’ (1980), art 1, http://www.oecd.org/digital/ieconomy/oecdguidelinesontheprotectionofprivacyandtransborderflowsofpersonaldata.htm.
[61] Kasneci D, ‘Data Protection Law: Recent Developments’ (DPhil thesis, Università degli studi di Trieste 2008) 17.
[62] Greenleaf G, ‘‘European’ Data Privacy Standards Implemented in Laws Outside Europe’ (2017) 149 Privacy Laws & Business International Report, 21; [2018] UNSWLRS 1. See also, Greenleaf G, ‘Asia’s Data Privacy Dilemmas 2014–19: National Divergences, Cross-Border Gridlock’ (2019) No 4, Revista Uruguaya de Protección de Datos Personales (Revista PDP) 49-73.
[63] Kirby M, ‘The History, Achievement and Future of the 1980 OECD Guidelines on Privacy’ (2010) 1 International Data Privacy Law 6.
[64] Ibid.
[65] Bloomberg Law, ‘The OECD Updates its 1980 Guidelines on the Protection of Privacy and Transborder Flows of Personal Data’ (10 October 2013), https://news.bloomberglaw.com/privacy-and-data-security/the-oecd-updates-its-1980-guidelines-on-the-protection-of-privacy-and-transborder-flows-of-personal-data.
[66] OECD, OECD Privacy Framework, 2013, forward, 4, https://www.oecd.org/sti/ieconomy/oecd_privacy_framework.pdf?_ga=2.13814448.628537204.1621868235-832121411.1621868235.
[67] OAS, ‘Who We Are’, Organization of American States, http://www.oas.org/en/about/who_we_are.asp, accessed 15 June 2020.
[68] Inter-American Commission on Human Rights, ‘Citizen Security and Human Rights’, http://www.cidh.org/countryrep/seguridad.eng/CitizenSecurity.V.a.htm, accessed 7 October 2021.
[69] OAS, ‘American Convention on Human Rights’, Organization of American States, 22 November 1969, https://www.cidh.oas.org/basicos/english/basic3.american%20convention.htm.
[70] Buergenthal T, ‘The American Convention on Human Rights: Illusions and Hopes’ (1971) 21 Buffalo Law Review 122.
[71] OAS, American Convention on Human Rights’ (n 69).
[72] Inter-American Court of Human Rights: Advisory Opinion-10/89, I-A. Court H.R., Series A: Judgments and Opinions, No. 10, 45 (1989).
[73] Mc Cullagh KM, ‘The Social, Cultural, Epistemological & Technical Basis of the Concept of ‘Private Data’’ (DPhil thesis, University of Manchester 2011) 71. See also, Munir AB, Yasin SHM and Karim ME, Data Protection Law in Asia (Sweet & Maxwell/ Thomson Reuters 2018), 62.
[74] Greenleaf G, ‘Five Years of the APEC Privacy Framework: Failure or Promise?’ (2009) 25 Computer Law & Security Review 28.
[75] See generally, Bulford C, ‘Between East and West: the APEC Privacy Framework and the Balance of International Data Flows’ (2007) 3 Journal of Law and Policy for the Information Society 709.
[76] APEC, ‘APEC Privacy Framework (2015)’ part iv, para 31, 38 (a) and 42, https://www.apec.org/Publications/2017/08/APEC-Privacy-Framework-(2015).
[77] Ibid, description.
[78] Ibid, additional definitions, 71, 72.
[79] Data Protection and Privacy Commissioners, ‘International Standards on the Protection of Personal Data and Privacy: The Madrid Resolution’ (2009) art. 2, http://privacyconference2011.org/htmls/adoptedResolutions/2009_Madrid/2009_M1.pdf.
[80] Ibid, art 16-18.
[81] Ibid, art 20-21.
[82] Ibid, art 19.
[83] Ibid, Part III, arts 6–11.
[84] See generally, Munir, Yasin and Karim (n 73) 67.
[85] ASEAN, ‘About ASEAN: Overview’, https://asean.org/about-us, accessed 14 October 2021.
[86] Association of Southeast Asian Nations (ASEAN), ASEAN Human Rights Declaration (adopted 18 November 2012), art 21, https://www.refworld.org/docid/50c9fea82.html.
[87] ASEAN, ‘Framework on Personal Data Protection’ (2016), art. 6 https://asean.org/wp-content/uploads/2012/05/10-ASEAN-Framework-on-PDP.pdf.
[88] Ibid, objectives, and effect of the framework, art 1-2.
[89] Van Alsenoy B, ‘Regulating Data Protection: The Allocation of Responsibility and Risk among Actors Involved in Personal Data Processing’ (DPhil thesis, KU Leuven University 2016) 103.
[90] Council of Europe, ‘A Convention to Protect Your Rights and Liberties’, https://www.coe.int/en/web/human-rights-convention, accessed 16 August 2020.
[91] Council of Europe, European Convention for the Protection of Human Rights and Fundamental Freedoms, as amended by Protocols Nos. 11 and 14, 4 November 1950, ETS 5, art 8, https://www.echr.coe.int/documents/convention_eng.pdf.
[92] Council of Europe, ‘The European Convention on Human Rights – How Does It Work?’, https://www.coe.int/en/web/impact-convention-human-rights/how-it-works, accessed 16 August 2020.
[93] Council of Europe, ‘Landmark Judgments’, https://www.coe.int/en/web/human-rights-convention/landmark-judgments,<< accessed 16 August 2020.
[94] Council of Europe, ‘Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data’ (Convention 108) (1981), https://rm.coe.int/1680078b37.
[95] Rule JB and Greenleaf GW, Global Privacy Protection: The First Generation (Edward Elgar Publishing 2010).
[96] Gutwirth S, Privacy and the Information Age (Rowman & Littlefield 2002) 90.
[97] Council of Europe, ‘Additional Protocol to the Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data, regarding Supervisory Authorities and Transborder Data Flows’ (2001), https://www.coe.int/en/web/conventions/full-list/-/conventions/treaty/181.
[98] Council of Europe (n 94).
[99] Greenleaf G, ‘The Influence of European Data Privacy Standards Outside Europe: Implications for Globalization of Convention 108’ (2012) 2 International Data Privacy Law 68.
[100] Giakoumopoulos C, Buttarelli G and O’ Flaherty M, Handbook on European Data Protection Law (European Union Agency for Fundamental Rights and Council of Europe, Luxembourg 2018) 26.
[101] See generally, Council of Europe, ‘Modernised Convention for the Protection of Individuals with Regard to the Processing of Personal Data’ (2018), (Convention 108+), https://search.coe.int/cm/Pages/result_details.aspx?ObjectId=09000016807c65bf.
[102] Iheanyi Nwankwo, ‘Modernized CoE Convention 108: A Global Standard on Data Protection’, IAPP (30 July 2018), https://iapp.org/news/a/modernized-coe-convention-108-a-global-standard-on-data-protection/.
[103] EU Directive 95/46: Directive 95/46/EC of the European Parliament and of the Council of 24 October 1995 on the Protection of Individuals with regard to the Processing of Personal Data and on the Free Movement of such Data, OJ 1995 L 281/31.
[104] Islam MT and Karim ME, ‘Extraterritorial Application of the EU General Data Protection Regulation: An International Law Perspective’ (2020) 28 IIUM Law Journal 531.
[105] Langheinrich M, ‘The Golden Age of Privacy?’ (2018) 17 IEEE Pervasive Computing 4.
[106] Hern A, ‘What Is GDPR and How will It Affect You?’, The Guardian (21 May 2018) https://www.theguardian.com/technology/2018/may/21/what-is-gdpr-and-how-will-it-affect-you.
[107] EU Commission, ‘Statement by Vice-President Ansip and Commissioner Jourová Ahead of the Entry into Application of the General Data Protection Regulation’ (24 June 2018), https://ec.europa.eu/commission/presscorner/detail/en/STATEMENT_18_3889.
[108] De Hert P and Czerniawski M, ‘Expanding the European Data Protection Scope beyond Territory: Article 3 of the General Data Protection Regulation in Its Wider Context’ (2016) 6 International Data Privacy Law 231.
[109] Facebook for Business, ‘What is the General Data Protection Regulation (GDPR)?’ https://www.facebook.com/business/gdpr, accessed 18 November 2020.
[110] Google, ‘We Are Committed to Complying with Applicable Data Protection Laws’ (Business and Data: Privacy Policy), https://privacy.google.com/businesses/compliance/, accessed 18 November 2020.
[111] Katie Collins, ‘Google Makes Privacy Policy Clearer than Ever to Comply with EU Law’ (May 11, 2018), https://www.cnet.com/news/google-makes-privacy-policy-clearer-than-ever-to-comply-with-eu-gdpr-law/.
[112] OHCHR, ‘Annual Thematic Reports of the Special Rapporteur on the Right to Privacy’ (2019) Report A/HRC/40/63, para 105: 17.
[113] Nymity, ‘Happy Birthday GDPR. At One Year on, What have We Learned?’, Lexology, 5 June 2019, https://www.lexology.com/library/detail.aspx?g=649cd552-7853-4abc-81c6-37af2c8dd415.
[114] Greenleaf G and Cottier B, ‘Data Privacy Laws and Bills: Growth in Africa, GDPR Influence’ (2018) 152 Privacy Laws & Business International Report, 11-13; UNSW Law Research Paper No. 18-52, 5.
[115] Ius Laboris, ‘The Impact of the GDPR Outside the EU’ (17 September 2019), https://theword.iuslaboris.com/hrlaw/whats-new/the-impact-of-the-gdpr-outside-the-eu, accessed 7 December 2020.
[116] Noordyke M, ‘US State Comprehensive Privacy Law Comparison’, IAPP (18 April 2019), https://iapp.org/news/a/us-state-comprehensive-privacy-law-comparison/.
[117] See generally, Rustad ML and Koenig TH, ‘Towards a Global Data Privacy Standard’ (2018) 71 Florida Law Review 365.
[118] Buttarelli G, ‘The EU GDPR as a Clarion Call for a New Global Digital Gold Standard’ (2016) 6 International Data Privacy Law 77.
[119] Schwartz PM, ‘Global Data Privacy: The EU Way’ (2019) 94 New York University Law Review.
[120] Rowland D and Macdonald E, Information Technology Law (Routledge-Cavendish 2005) 299.
[121] Van Alsenoy (n 89).
[122] Huth D, ‘A Pattern Catalog for GDPR Compliant Data Protection’ (2017), In PoEM Doctoral Consortium 34-40.
[123] Hessisches Datenschutzgesetz [HDSG] [Hessian Data Protection Act], Hess GVB1. I 625 (1970); Simitis S, ‘Privacy—An Endless Debate?’ (2010) 98 California Law Review 1995; Kirby MD, ‘Transborder Data Flows and the Basic Rules of Data Privacy’ (1980) 16 Stanford Journal of International Law 39. See also, Bygrave LA, Data Privacy Law: An International Perspective (Oxford University Press 2014) 99.
[124] Greenleaf G and Cottier B, ‘2020 End a Decade of 62 New Data Privacy Laws’ (2020) 163 Privacy Laws & Business International Report 24-26, 1, https://ssrn.com/abstract=3572611.
[125] Ibid.
[126] Bennett C, ‘The Governance of Privacy: New Zealand in Global Perspective’, Privacy Awareness Week, Wellington, New Zealand, 5 May 2010, http://www.colinbennett.ca/Presentations/WellingtonMay2010.pdf; see also, Singh R, Legalization of Privacy and Personal Data Governance: Feasibility Assessment for a New Global Framework Development’ (DPhil thesis, University of Ottawa 2016) 32.
[127] Banisar D and Davies S, ‘Global Trends in Privacy Protection: An International Survey of Privacy, Data Protection, and Surveillance Laws and Developments’ (1999) 18 The John Marshall Journal of Information Technology Privacy Law 1.
[128] Westin ‘Social and Political Dimensions of Privacy’ (n 6) 7.
